M.E.T.T.S. - Consulting Engineers > White Papers > Business Continuity Management and the Terrorist Threat
Business Continuity Management and the Terrorist Threat
Dr. Michael C. Clarke, CPEng, FIEAust, FAusIMM, RPEQ
CEO, M.E.T.T.S. Pty. Ltd.
Consulting Engineers, Resource Management and Infrastructure Development
Gold Coast, QLD, Australia
Email: metts[at]metts.com.au
Share this page:
Business Continuity Management (BCM) in Australia has been addressed in the Australian Standards Association's handbook, HB 221:2003. The handbook looks at threats to business continuity from natural disasters, corporate collapses, war and terrorism. It provides good guidance in terms of risk assessment and the devising of business continuity plans that will lessen the impact of events that threaten a business or organisation.
The first page of the handbook does address terrorism in terms of it being a hazard which business might face. Other than mentioning the problems of the New York Workers Compensation Board in processing excessive claims following the terrorist event of September 11 2001, it does not specifically address terrorism as a specific threat that may have dimensions greater than what could be expected from natural disasters.
Terrorism can have considerable effects and ramifications on business. These include, the movement away from just-in-time supply for manufacturing and the increases in business inventories, changes in the quality management systems to ensure timely and continuous supply, changes in the choice of suppliers and partners in manufacture, new precautions to ensure key-person protection, and changes in priorities vis-à-vis security taking a greater portion of resources.
Tools for Business Continuity Management include risk assessment and risk management. These tools can be applied to the terrorism threat as well as other hazards. The application of the risk tools to countering terrorism must however include an analysis of why a specific business could be of interest to terrorists. It must further address the similar threat levels to the supply and output chains on which a business relies.
Best Practice Counter Terrorism Management (BPCTM).
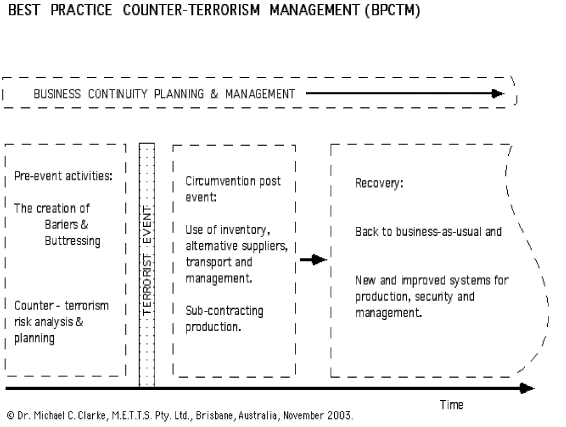
The development of BPCTM will involve the use of risk analysis and thence management to determine the vulnerabilities of a business. The delineation and estimation of acute specific threats can be part of a security analysis and can be deferred to security experts and law enforcement. The planning for circumvention and recovery from a terrorist event is however the responsibility of management and those professionals, engineers, technocrats and accountants, who know the business and know what are the priorities.
A terrorist event may be aimed at disrupting business by breaking the chain of supply or output. It may not be an attack on the principle target but on an auxiliary target that is crucial to the operation of the key organisation. Thus an attack on an armament manufacturer may be directed at a supplier of key components, and an attack on a Genetically Modified (GM) seed developer may be on the provider of the organisation's laboratory technology.
September 11, demonstrated how a group and engineers and other technocrats were able to organise a successful terrorist attack that took years of planning. They, the terrorist-engineers, utilised the tools of engineering to plan, resource, secure and carry out their mission. The attack was a good example of project planning with a sizeable use of risk management. Similar attacks by other motivated terrorists could use project planning and risk assessment to cripple an organisation. The crippling could take many forms, and could include disruption to communications and transport, the sabotaging of inputs and inventory, the sabotaging of product and the removal of key personnel.
At each stage of supply, production or distribution, there could be opportunities for attack. In some cases the terrorist attack my be nothing more that the actions of disgruntled employees, in other cases it may be actions of groups external to the organisation or region, but who see the target organisation's demise as being complementary to their goals. In either case the attackers will likely have a detailed knowledge of an organisation's operations and will have an understanding of strengths and vulnerabilities.
The Content of Best Practice Counter Terrorism Management
Security procedures will be one aspect of BPCTM. In this case expertise can be found to analyse the risk in terms of external and internal factors. The external factors include the political regime in which an organisation exists (eg Australia v's New Zealand), its ownership and foreign loyalties, its position regarding export trade and the international view of its products (eg if it deals in GM produce). The internal factors may include labour relations, funding sources (legitimate or not) and management style.
The engineering of securing critical infrastructure will be another important aspect. Two sub categories exist here. The first is the creation of barriers around critical infrastructure and the second is buttressing such infrastructure. Barriers are useful in preventing a terrorist approaching a target, and have the psychological effect of making a potential target look too hard to assault. The putting of any specific target in a terrorist's too hard basket is probably a good use of resources in specific instances.
Barriers and buttressing are practical around some notable examples of critical infrastructure. One such example is the new research reactor at Lucas Heights. The reactor, being a relatively small piece of infrastructure, has (or will have) multiple layers of barriers. The reactor can be buttressed by increasing the strength of the containment building and more importantly the strength of the relatively very small reactor vessel itself. The creation of effective barriers and buttressing for such icons as the Sydney Harbour Bridge and the Sydney Opera House would be a lot more difficult.
Engineering can have another role in counter terrorism. That role is in providing good risk assessment of, structures, production systems and operating systems. In some cases that risk assessment will lead to risk management decisions that may include, the abandonment of just-in-time supply and manufacturing, the creation of greater buffers in inventory, the pre-production inspection of inputs for sabotage, the post-production inspection of product for sabotage, and the creation of production redundancy capacity.
The planning to 'accommodate' the terrorist threat by engineers in association with business managers and accountants will be required by organisations wishing to provide continuity of service and operation following an attack. Circumvention of the effects and results of a terrorist attack are important, and can provide for immediate continuity. The circumvention may include using residual production capacity, using and rationing existing inventory, switching suppliers and supply chains, switching product distribution chains, using 'head shops' for supplying temporary labour and management, and sub-contracting other organisations to supply services and product.
The last aspect is turning circumvention into recovery and business-as-usual - see figure. Recovery is dealt with in the Standards Handbook 221:2003. Recovery procedures will be common to all types of business disruption, since in most circumstances time will be available to repair the damage, and to actually improve the organisation's systems and management.
In BPCTM the costs, outside those of other BCM, will be in the areas of providing security, additional barriers and buttressing needed for terrorist threats, and for planning circumvention. Risk analysis and thence risk management will be required for setting priorities and in working towards a cost/benefit analysis. The cost of barriers and buttressing may be partially off-set by lower insurance premiums, whilst there may be some security return from being able to demonstrate to clients that precautions are in place to help ensure business continuity.
The costs of planning and carrying out circumvention may be considerable. The cost of keeping additional inventories of resources, feed stocks and product includes the costs of additional warehousing (and its security), more management of stock (rotation and quality control) and the interest chargeable on the value of the materials and production. Providing redundancy in production will also be costly, and may require the installation of plant at multiple locations. Redundancy in transport, materials supply (keeping alternative suppliers happy with a share of the input) and management will also be costly.
The Application of BPCTM: Two Examples.
A hypothetical example of BPCTM would be for a defense and aeronautical telecommunications manufacturer. The manufacturer supplies both military and civil aviation equipment to local and international customers. Some sub-components are made in Israel and some product is sold to Israel via the United States. (The Israeli components are badged with another country of origin being the 'source', but employees, competitors, transport agents and customers know the real origin of the components. The company is known to be 'friendly' to Israel.)
The company has taken good security precautions at its main plant in Sydney, but relies on a number of general electrical component suppliers for around 70% of its total output. The local component suppliers have varying levels of security, but their management does not consider the terrorist risk to their very non-controversial operations a serious hazard, and thus overall they have light security.
In terms of externalities, the company's exposure to terrorist action in Israel that may disrupt the export of vital components to Australia is a risk. The 'known' relationship of the company to Israeli interests is another risk. The direct risk in Australia is reduced by good security procedures, but the indirect risk to relatively unprotected sub-contracted Australian suppliers is real.
The company could reduce its international exposure by finding sub-component suppliers outside Israel, but could lose US contracts if it did so. The company could increase its inventory of critical sub-components sourced from Israel, at the risk of some stock becoming obsolete whilst in storage. Directions could be given to local suppliers to become more security conscious and/or keep larger inventories in secure locations.
Following a major risk analysis, a risk management plan is developed that has the following features:
• the company to secure its Sydney manufacturing facility with further counter-terrorism measures, including more rigorous checks on employees,
• Israel will continue to supply components, but the inventory of such components will increase to cover eight months production instead of two months,
• the company will spread it purchasing of local components around other manufacturers and wholesalers, and increase its local component inventory from one month's production to two, and
• the company will provide security training for key personnel, and assist them with backing-up electronic data.
A redundant or stand-by alternative manufacturing plant could be constructed to maintain production continuity in case of an attack on the main plant, but given the high security of the principal manufacturing operation, this precaution appears excessive at the present level of risk.
As a second example a hypothetical GM oil seed breeder is used. This company has originally imported GM seed from overseas, and it has had it trial plots attacked by environmentalists. The company has spent considerable resources in further modifying one of its GM products to withstand a local pest (not an environmentalist!).
The company has reasonably secured its main laboratory, but its trial plots are difficult to secure. Some staff at the laboratory and the trial areas may have qualms regarding the introduction of GM technology into the food-chain.
Again following a major risk assessment, a risk management plan is developed that has the following features:
• Redundancy in both the laboratory function and trial plots is decided upon. Some of the new GM material will be transferred to associated laboratories, and the number of field trials will be doubled, with some trials being solely managed by the associated laboratories, and
• more rigorous checks will be made of employees and management, and a system of segregation of research and management areas on the main laboratory will be enforced.
In the examples above we have planning for countering a terrorist threat, and planning for circumventing the effect and impact of a terrorist action. The result in both cases would be an increase in business continuity confidence, but also there would be an increase in the costs of production.
Conclusion.
It is recommended that a corollary to HB 221:2003 be produced that looks specifically at the terrorist threat in terms providing barriers and buttressing to critical infrastructure to ward off the threat, and in providing circumvention planning in case a terrorist event occurs.
BPCTM Diagram:
NOTE:
You are welcome to quote up to a maximum of three paragraphs from the above white paper, on condition that you include attribution to this website, as follows:
SOURCE: M.E.T.T.S. Pty. Ltd. Website http://www.metts.com.au
Share this page:
Author: Michael C Clarke
(Michael C Clarke on Google+)
M.E.T.T.S. Pty. Ltd. - Consulting Engineers PO Box 843, Helensvale QLD 4212, Australia TEL: (07) 5502 8093 • (Int'l) +61-7-5502 8093 EMAIL: metts[at]metts.com.au Copyright • Privacy • Terms of Use © 1999-2014 M.E.T.T.S. Pty. Ltd. All Rights Reserved. |
.

